Minimum Viable Secure Product

Available on Community subscription plan.
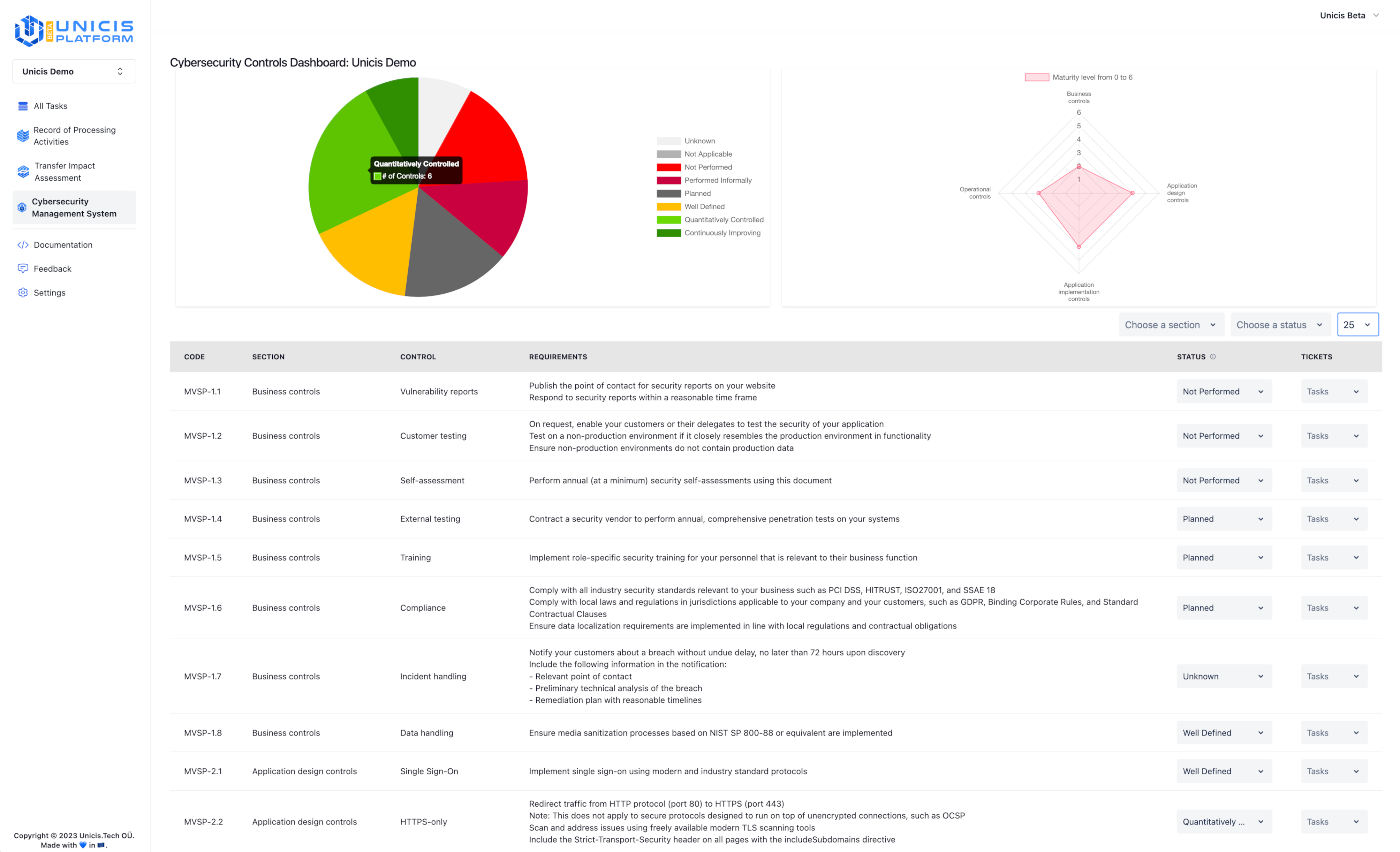
Minimum Viable Secure Product (MVSP) Available is a security checklist for B2B software and business process outsourcing vendors. The checklist is created with simplicity in mind, containing only those measures that must be put in to assure a product's least feasible security posture. We propose that all organizations developing B2B software or otherwise managing sensitive information implement at least the following procedures, and are strongly encouraged to go well beyond these in their security programs. Along with other well-known organizations such as SalesForce, Google, Okta, Slack, Secureframe, Safebase, and others, Unicis is a partner and contributor.
MVSP Resources:
What is its purpose?
It can be used for a variety of reasons, but the most common are those listed below.
Requests for proposals
The documentation for MVSP controls is brief and easy to understand. Can give you a common cybersecurity benchmark for choosing vendors and makes the duties of the sourcing teams easier.
Self-assessments
Startups and SMEs that aren't yet established enough to invest in costly international compliance initiatives like ISO 27001, SOC 2, or PCI DSS might use MVSP as a starting point to guarantee the security posture of their MVP.
Third-party security
In order to determine whether you are taking care of security and have poor corporate cyber hygiene, large firms who want to become clients, partners, or customers try to triage vendor security posture surveys.
Industries
Any organization that build or offer enterprise software and services—such as technology, healthcare, finance, government, education, retail, telecom, and legal—especially where sensitive or regulated data is processed or stored.
Unicis solution
The MVSP checklist and controls have been implemented into the following Unicis apps.